After changing settings on my Wireless router to WEP (for TESTING PURPOSES only), I downloaded Slitaz Linux, and wrote it to bootable USB Flash stick.
This distribution is very interesting, as Slitaz-3.0 is just 30MB in size (downloadable ISO image).
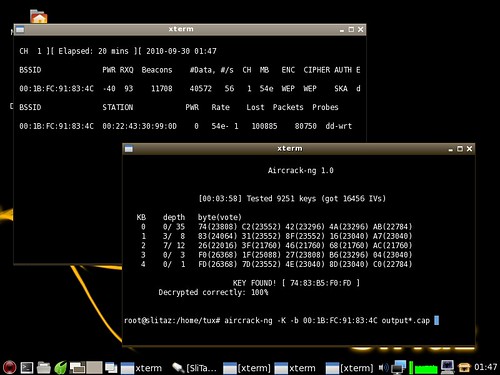
Slitaz Linux is USB stick bootable version of Linux, which is easy to use for security assessment. Many people do not realize how insecure is their Wireless connection. In most cases they think that putting "some" security is enough. And that's WEP.
You can see on screenshot above that it took just 3 min. 58 seconds to crack WEP key!
And this was done using old, aged laptop with rather weak built-in wireless adapter.
To get things running, I had to install aircrack-ng package manually (#tazpkg get-install
Setup for Wireless Access Point
Hardware (Access Point): ASUS WL-500G Premium v1, 802.11g/54Mbps, flashed with DD-Wrt v24-sp2 (10/10/09) mega. You can check Mac address
In fact, it's irrelevant what brand of AP or Wireless Router you have.
If you selected WEP for "securing your wireless connection", than you are vulnerable.
I just gave detailed description of hardware used, as some people may be curious about that.
Wireless client (Station): ASUS notebook. According to OUI Search, adapter has been made by AzureWave Technologies.
All equipment is mine, Router (AP) was located 1.5 m from Wireless Client during my tests.
PROTECT YOURSELF, DON'T USE WEP ENCRYPTION!
USE WPA-PSK or BETTER WPA2-PSK!
среда, 13 октября 2010 г.
Slitaz Linux: WEP key found!
Подписаться на:
Комментарии к сообщению (Atom)
Комментариев нет:
Отправить комментарий