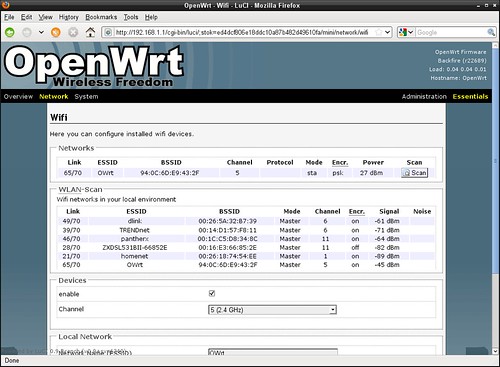
OpenWrt: Client mode. Scan networks
OpenWrt: режим Клиент беспроводной сети. Сканирование доступных беспроводных сетей.
среда, 27 октября 2010 г.
OpenWrt: Client mode. Scan networks
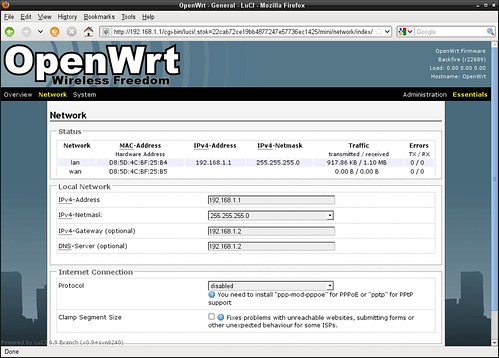
OpenWrt Network Configuration.
Internet Connection is disabled in my setup.
LAN IP address of this router: 192.168.1.1
Internet Gateway: 192.168.1.2
DNS Server: 192.168.1.2
Host: Wireless Router TP-Link WR841ND
Chipset: Atheros AR7240
Processor architecture: MIPS 24Kc v7.4
***
OpenWrt - настройки сети.
Режим "Шлюз для доступа в Интернет" (Internet Gateway) выключен.
LAN IP-адрес маршрутизатора: 192.168.1.1
Интенет-шлюз: 192.168.1.2
DNS сервер: 192.168.1.2
Хост-система: беспроводный маршрутизатор TP-Link WR841ND.
Чипсет: Atheros AR7240.
Процессорная архитектура: MIPS 24Kc v7.4
OpenWrt: SSH Login using PUTTY
You can login to your OpenWrt router using PUTTY program (Windows)
This system uses:
- Linux kernel 2.6.32.16
- BusyBox v1.15.3
***
К маршрутизатору с прошивкой OpenWrt можно подключиться по сети, используя программу PUTTY (для Windows)
Эта прошивка (firmware) использует:
- Linux kernel 2.6.32.16
- BusyBox v1.15.3
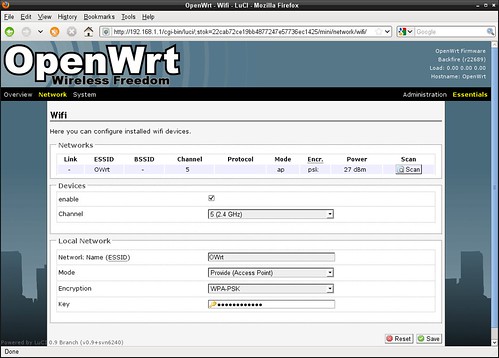
OpenWrt - WiFi Network configuration
OpenWrt - wireless interface configured as Access Point.
Security: WPA-PSK
OpenWrt - беспроводный интерфейс сконфигурирован как Точка доступа.
Настройки безопасности: WPA-PSK
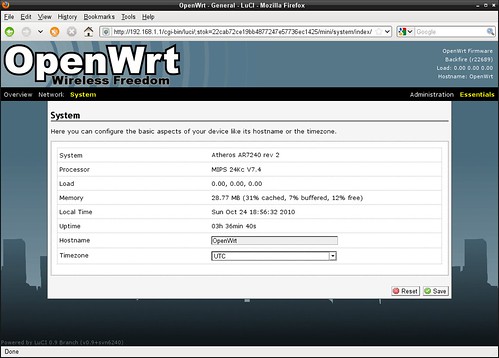
OpenWrt running on TP-Link WR841ND Wireless Router
OpenWrt Backfire 10.03.1-RC3 running on TP-Link WR841ND Wireless Router.
This router uses Atheros AR7240 chipset. Processor architecture is MIPS 24Kc v7.4
System information
I have flashed it with OpenWrt using standard web interface.
***
OpenWrt Backfire 10.03.1-RC3 работает на беспроводном маршрутизаторе TP-Link WR841ND.
Маршрутизатор использует чипсет Atheros AR7240. Процессорная архитектура - MIPS 24Kc v7.4
Страница Системная информация
Я сменил прошивку в маршрутизаторе TP-Link WR841ND
со стандартной на OpenWrt используя веб-интерфейс.
Использование tftp не потребовалось.
среда, 20 октября 2010 г.
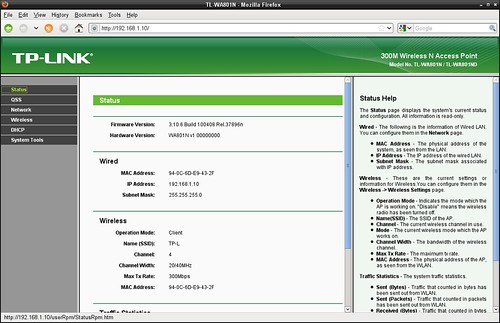
TP-Link TL-WA801ND Wireless Access Point. Status page
TP-Link TL-WA801ND Wireless Access Point.
Status page.
Hardware version is WA801N v1
I bought this WAP to upgrade my Home LAN (WLAN) to 300Mbps 802.11n. And to study in details design of modern wireless Access Point based on Atheros chipset.
After "playing" with standard firmware provided by TP-Link, I plan to flash it with OpenWRT firmware, or other Open Source firmware/Embedded Linux.
Purpose of this post (and photos on Flickr) is to make short review of router "as it is", and make snapshots how User Interface looks.
Hardware itself is similar to TL-WR841ND Wireless Router which is part of my new setup / environment.
You may also note that WA841ND WAP is already connected to WR841ND router as Client (Wireless STA)
More detailed description what is this product about:
Wireless 802.11N Access Points are designed to deploy or expand high-speed wireless N network. Different devices like Desktop PCs, Laptops, Game Сonsoles, Smartphones, Printers, or Network Attached Storage can be connected together using high-speed 802.11n wireless network.
The TL-WA801ND Access Points can use Repeater Mode to expand the coverage and signal strength for the current wireless environment with Wireless Distribution Service (WDS) technology by connecting multiple Access Points. Universal Repeater Mode allows to connect together APs and Routers without WDS support. Users can use those features to deploy large-scale wireless network , and improve connectivity in remote areas.
Features
* Support for Wireless 802.11n standard with up to 300Mbps connection speed
* Backward compatible with 802.11g and 802.11b standards
* 2T2R MIMO technology provides robust high-bandwidth wireless Tx/Rx capability with an extended range
* CCA™ improves wireless performance while automatically avoiding channel conflict
* Easily setup a WPA encrypted secure connection at a push of the QSS button
* Supports Wi-Fi Multimedia (WMM) assures the quality of VoIP and multimedia streaming
* Supports multiple operating modes (Access Point, Client, Universal Repeater, WDS Repeater, Point to Point, Point to Multi-Point Bridge)
* Supports up to 30 meters of Power over Ethernet capability for flexible deployment
* Multi-SSID: up to 4 SSIDs and VLAN support, it allows to provide greater security and differentiated services for different user groups
* Support for WPA / WPA2 encryption for better security
* Detachable Antenna allows to extend coverage and provide stronger signal, using external hi-gain antennas
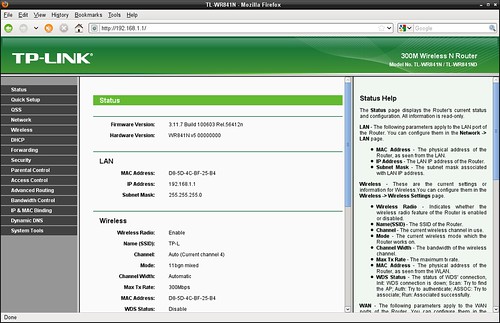
TP-Link TL-WR841ND Wireless Router. Status Page
TP-Link TL-WR841ND Wireless Router.
Status page.
Hardware version is WR841N v5
I bought this router to upgrade my Home LAN to 300Mbps 802.11n. And to study in details design of modern wireless router based on Atheros chipset.
After "playing" with standard firmware provided by TP-Link, I plan to flash it with OpenWRT firmware, or other Open Source firmware/Embedded Linux.
Purpose of this post (and photos on Flickr) is to make short review of router "as it is", and make snapshots how User Interface looks.
More detailed description what is this product about:
The TL-WR841ND Wireless N Router is a combined Wired / Wireless network connection device designed specifically for small business, office, and home office networking
Such kind of device is also known as Internet Gateway Device (IGD), or Residential Gateway, as its typical usage scenario is to provide Internet connectivity for several (up to hundred) users - PC Desktop, Mac, Laptop, Smartphone, Game Console, Media Server, etc., using just one IP address from ISP.
Specifications:
- IEEE 802.11n standard with wireless transmission speeds of up to 300Mbit.
- Backward compatible with 802.11g and 802.11b standards
- 2T2R MIMO technology provides robust high-bandwidth wireless Tx/Rx capability with an extended range
- Two External Detachable Antennas for better wireless performance, transmission rates, stability and coverage.
- CCA technology automatically avoids channel conflicts using its channel selection feature.
- Easily setup a WPA encrypted secure connection at a push of the QSS button
- Supports Wi-Fi Multimedia (WMM) assures the quality of VoIP and multimedia streaming
- Support for WPA / WPA2 encryption for better security
- Universal Plug and Play support allows UPnP-enabled programs (like BitTorrent, KTorrent) to open ports on router automatically. You don't need to do Port Forwarding manually if you use UPnP.
среда, 13 октября 2010 г.
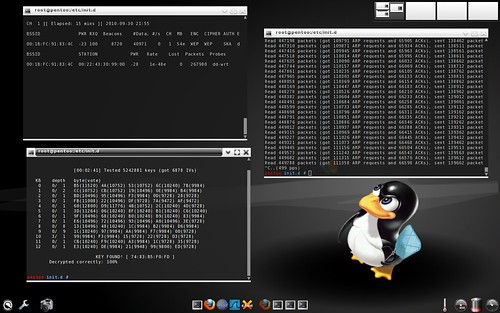
Pentoo Linux: WEP key found!
Next try was Pentoo Linux. I downloaded it and wrote it to bootable USB Flash stick.
It is bigger in size comparing to Slitaz Linux (682MB downloadable ISO image), but has better support for modern graphics adapters, and more tools packaged.
Latest version Pentoo 2009.0 final has kernel 2.6.31.6 and "wifi stack 2.6.32_rc7 with injection and fragmentation patches".
Pentoo Linux, variation of Gentoo Linux, is USB stick bootable version of Linux, which is easy to use for security assessment.
Many people do not realize how insecure is their Wireless connection. In most cases they think that putting "some" security is enough. And that's WEP.
You can see on screenshot above that it took just 3 min. 58 seconds to crack WEP key!
And this was done using old, aged laptop with rather weak built-in wireless adapter.
To get things running, you need to enable (start) networking manually. This was probably the most complex task in my test, as networking in Pentoo/Gentoo is different from Fedora/OpenSUSE/Mandriva, and you won't find here NetworkManager or DrakNet.
Than I followed instructions on Aircrack Simple WEP crack page.
Setup for Wireless Access Point
Hardware (Access Point): ASUS WL-500G Premium v1, 802.11g/54Mbps, flashed with DD-Wrt v24-sp2 (10/10/09) mega. You can check Mac address
In fact, it's irrelevant what brand of AP or Wireless Router you have.
If you selected WEP for "securing your wireless connection", than you are vulnerable.
I just gave detailed description of hardware used, as some people may be curious about that.
Wireless client (Station): ASUS notebook. According to OUI Search, adapter has been made by AzureWave Technologies.
All equipment is mine, Router (AP) was located 1.5 m from Wireless Client during my tests.
PROTECT YOURSELF, DON'T USE WEP ENCRYPTION!
USE WPA-PSK or BETTER WPA2-PSK!
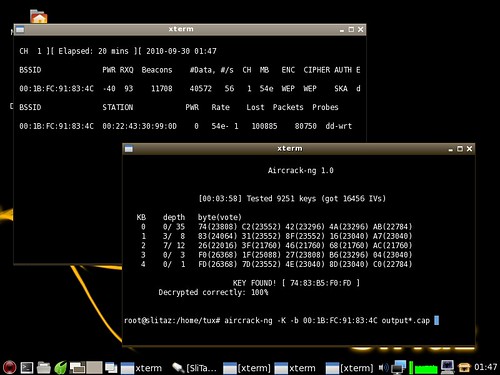
Slitaz Linux: WEP key found!
After changing settings on my Wireless router to WEP (for TESTING PURPOSES only), I downloaded Slitaz Linux, and wrote it to bootable USB Flash stick.
This distribution is very interesting, as Slitaz-3.0 is just 30MB in size (downloadable ISO image).
Slitaz Linux is USB stick bootable version of Linux, which is easy to use for security assessment. Many people do not realize how insecure is their Wireless connection. In most cases they think that putting "some" security is enough. And that's WEP.
You can see on screenshot above that it took just 3 min. 58 seconds to crack WEP key!
And this was done using old, aged laptop with rather weak built-in wireless adapter.
To get things running, I had to install aircrack-ng package manually (#tazpkg get-install
Setup for Wireless Access Point
Hardware (Access Point): ASUS WL-500G Premium v1, 802.11g/54Mbps, flashed with DD-Wrt v24-sp2 (10/10/09) mega. You can check Mac address
In fact, it's irrelevant what brand of AP or Wireless Router you have.
If you selected WEP for "securing your wireless connection", than you are vulnerable.
I just gave detailed description of hardware used, as some people may be curious about that.
Wireless client (Station): ASUS notebook. According to OUI Search, adapter has been made by AzureWave Technologies.
All equipment is mine, Router (AP) was located 1.5 m from Wireless Client during my tests.
PROTECT YOURSELF, DON'T USE WEP ENCRYPTION!
USE WPA-PSK or BETTER WPA2-PSK!
DD-Wrt WEP settings
There are many myths and articles circulating around about Wireless security (insecurity?). Google search about "WEP crack" brings articles dated by 12 Aug 2001 or so.
Or web pages with with materials readable only by real geek.
Technicians familiar with IP networking usually provide general answers like "WEP is insecure".
But how much it is insecure? And does it matter for you, typical owner of Home ADSL router or Wireless Access Point?
That's a good question, in my opinion.
So I did some research on my own.
Before going further, I ave to admit that I am familiar with Computer Networking , being working in IT industry for 15 years, and last 8 years in Networking companies. But on management positions.
This page shows DD-Wrt setup page for Wireless Security.
IMPORTANT NOTE: this setup was used only for testing, for a very short time, I would never use WEP for real deployment for myself, or recommend it to someone else.
If you have no choice (in your old Router or Access Point, or aged Wireless Client device) but WEP - than ... do not use Wireless at all!